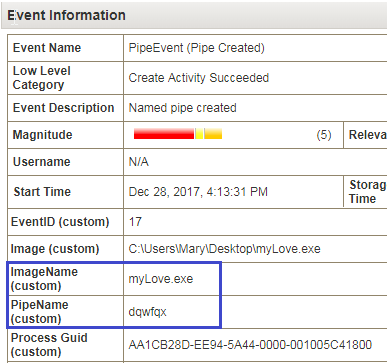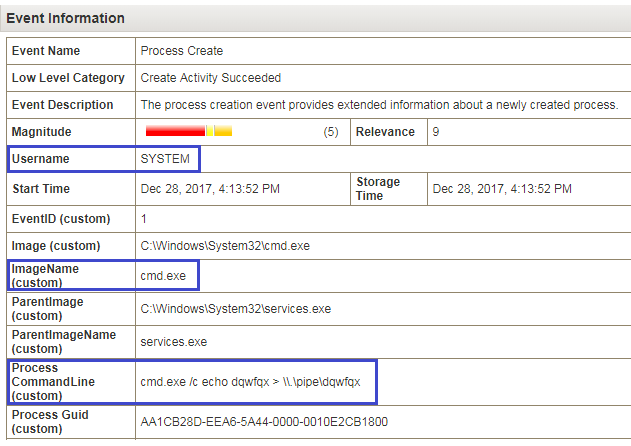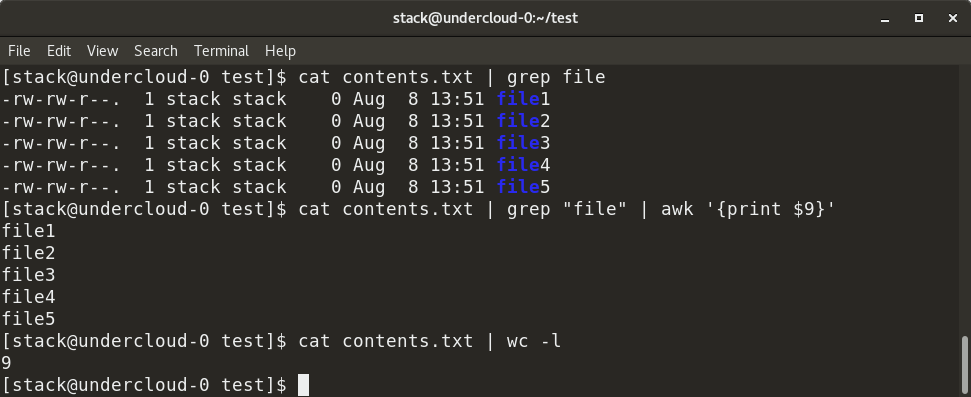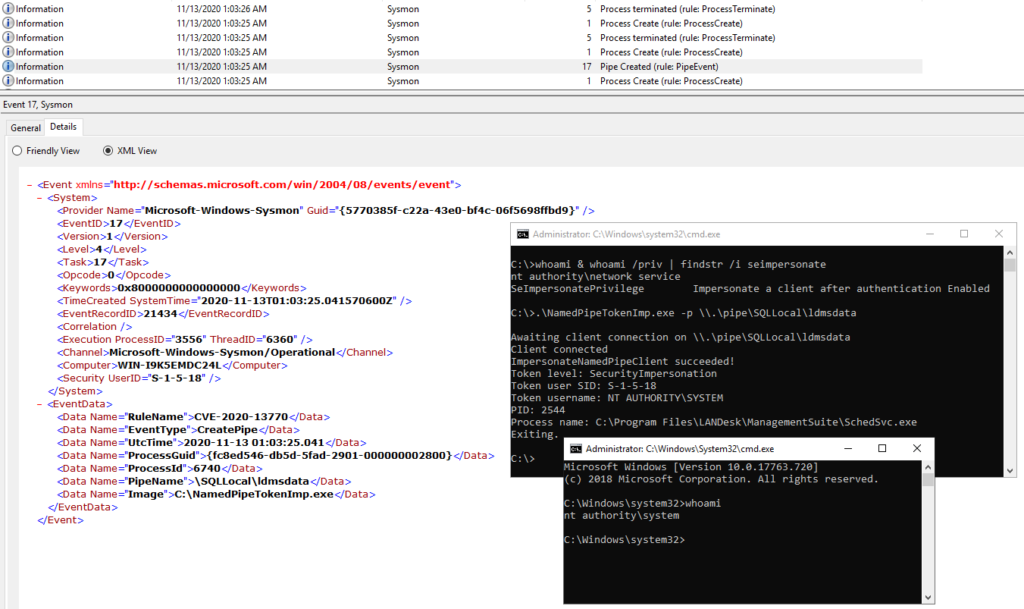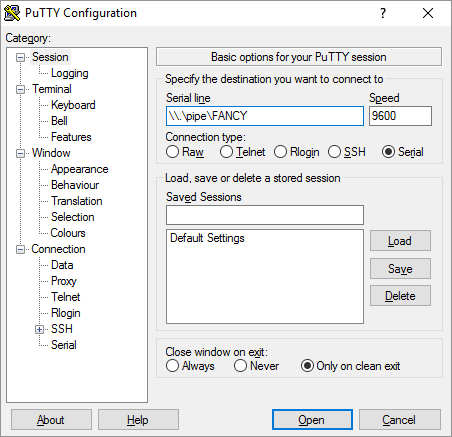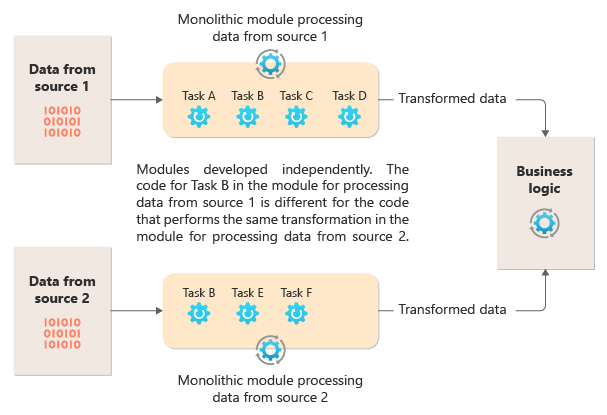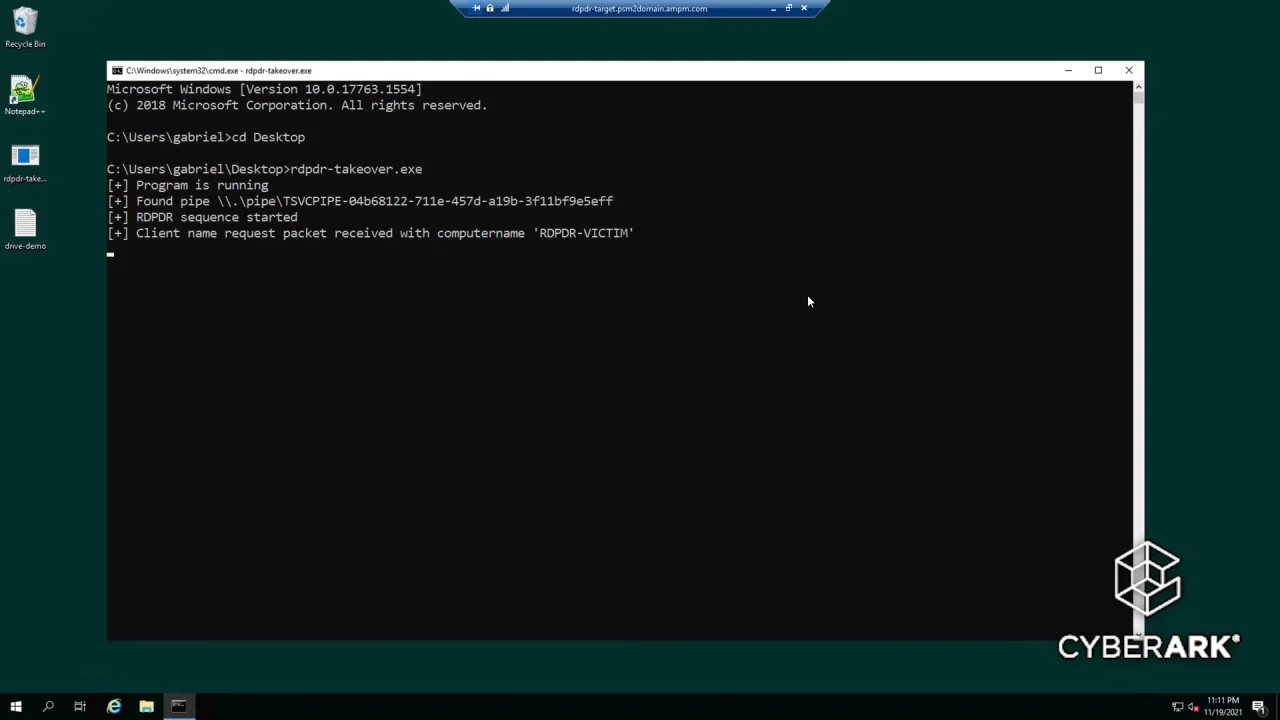
Attacking RDP from Inside: How we abused named pipes for smart-card hijacking, unauthorized file sys

windbg - How to create a serial pipe between a windows host and virtual machine in VirtualBox 5.2x version? - Stack Overflow
Windows named pipe error: The system cannot find the file specified. (code: 2) · Issue #165 · samtecspg/conveyor · GitHub
GitHub - ianculovici/Windows-Named-Pipes-Shell: Windows named pipe create from C# communicating with a shell command. The example uses MORE.




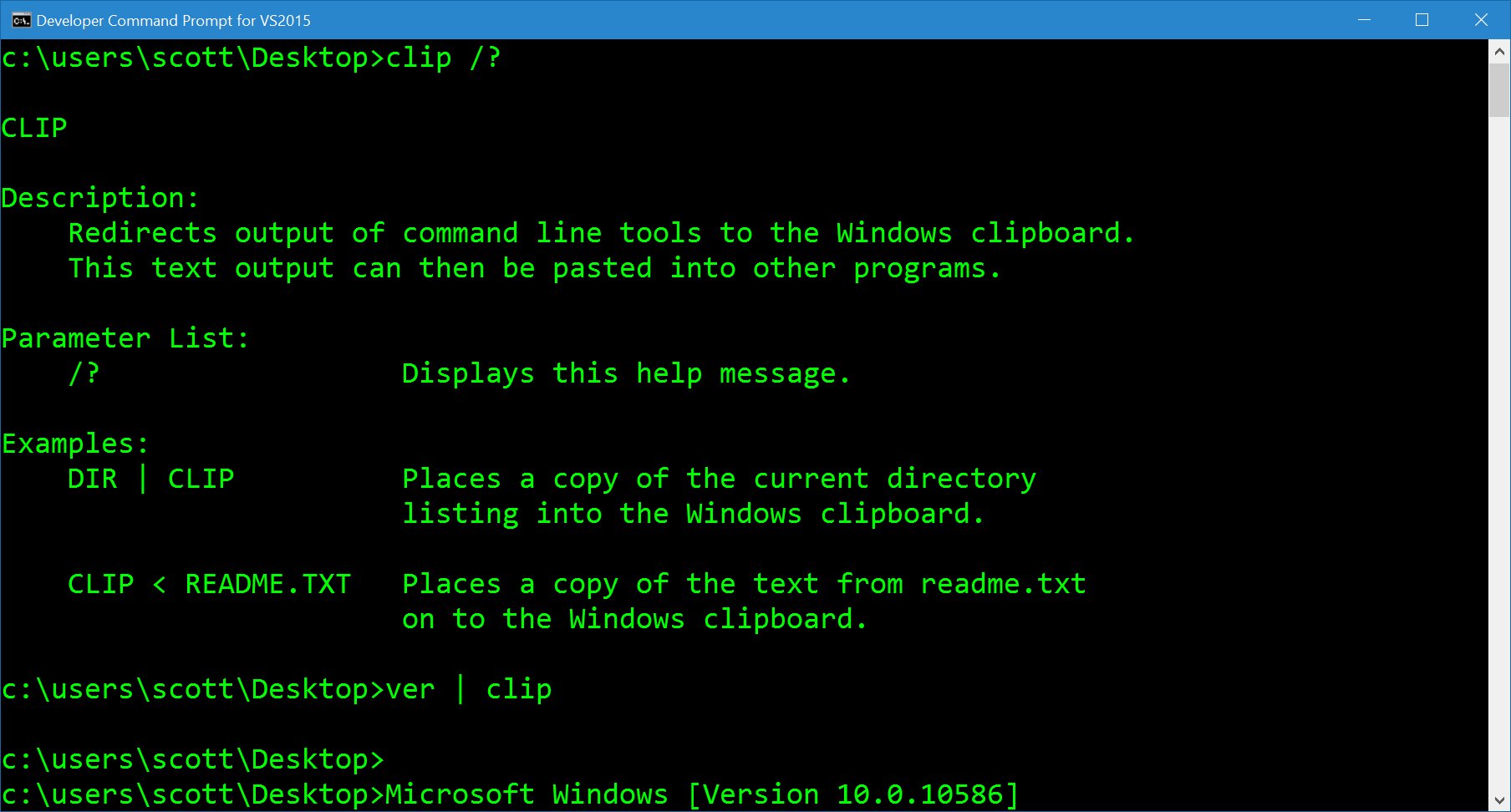


![MS-SMB2]: Executing an Operation on a Named Pipe | Microsoft Learn MS-SMB2]: Executing an Operation on a Named Pipe | Microsoft Learn](https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-smb2/ms-smb2_files/image009.png)